Police departments must meet federal cybersecurity standards to access important databases

Police departments without proper cyber security measures in place could lose access to valuable state and federal databases that provide information about sex offenders, warrants, licensing data, missing persons reports, gang and terrorist watchlists, criminal histories, and other important data.

The FBI’s Criminal Justice Information Services (CJIS) has modernized its own security policy to better align with the National Institute of Standards and Technology (NIST) framework as well as protect important data from cyber criminals. This database includes finger printing, the National Criminal Information Center (NCIC), and other resources the FBI makes available to state and local law enforcement.
The CJIS database also funnels information into state databases, such as the TBI’s Tennessee Incident Based Reporting System (TIBRS).
VC3 Account Executive McKenzie Walton discussed how these new policies could impact police departments across the state at TML’s Legislative Conference in Nashville. Walton said departments could lose access to valuable data if they or vendors who serve their agency for cybersecurity are not in compliance with the new FBI CJIS Security Policy.
“What that means for your municipality is that you cannot do national crime background checks, look at fingerprints or the sex offender registry,” Walton said. “That is all accessed through TBI databased, which are mandated by CJIJS. Municipalities are frequent focuses of cyberattacks due to their limited budgets. Being in compliance with these measures are super important. We need to start the compliance process. The worst thing that could happen is the TBI comes in and does an audit, finds you aren’t in compliance, and you no longer have access to these resources you desperately need to have a functioning police department. You can also be fined or be breached.”
 Walton said a municipality she works with recently had their police department’s computer systems breached and all of the police reports were frozen. Not only did the department itself not have access to the reports but local court proceedings requiring those reports could not take place.
Walton said a municipality she works with recently had their police department’s computer systems breached and all of the police reports were frozen. Not only did the department itself not have access to the reports but local court proceedings requiring those reports could not take place.
Breaches in police data can also compromise public trust and put cities at risk for lawsuits and cases having to be dismissed because of a data breach.
“If there is a data breach, it is very likely that a very good lawyer can go to court and say evidence is inadmissible because of that breach,” she said. “There are also chain of custody issues. Another big concern is that if you aren’t in compliance with CJIS, you cannot apply for federal criminal justice grants.”
Not being able to access these databases can also compromise cooperation with other law enforcement agencies.
“You need to be able to talk to your other colleagues throughout other departments,” Walton said. “If an officer pulls someone over, they won’t be able to see if that person has warrants out from anywhere. This allows everyone to talk to each other and allows more efficiency.”
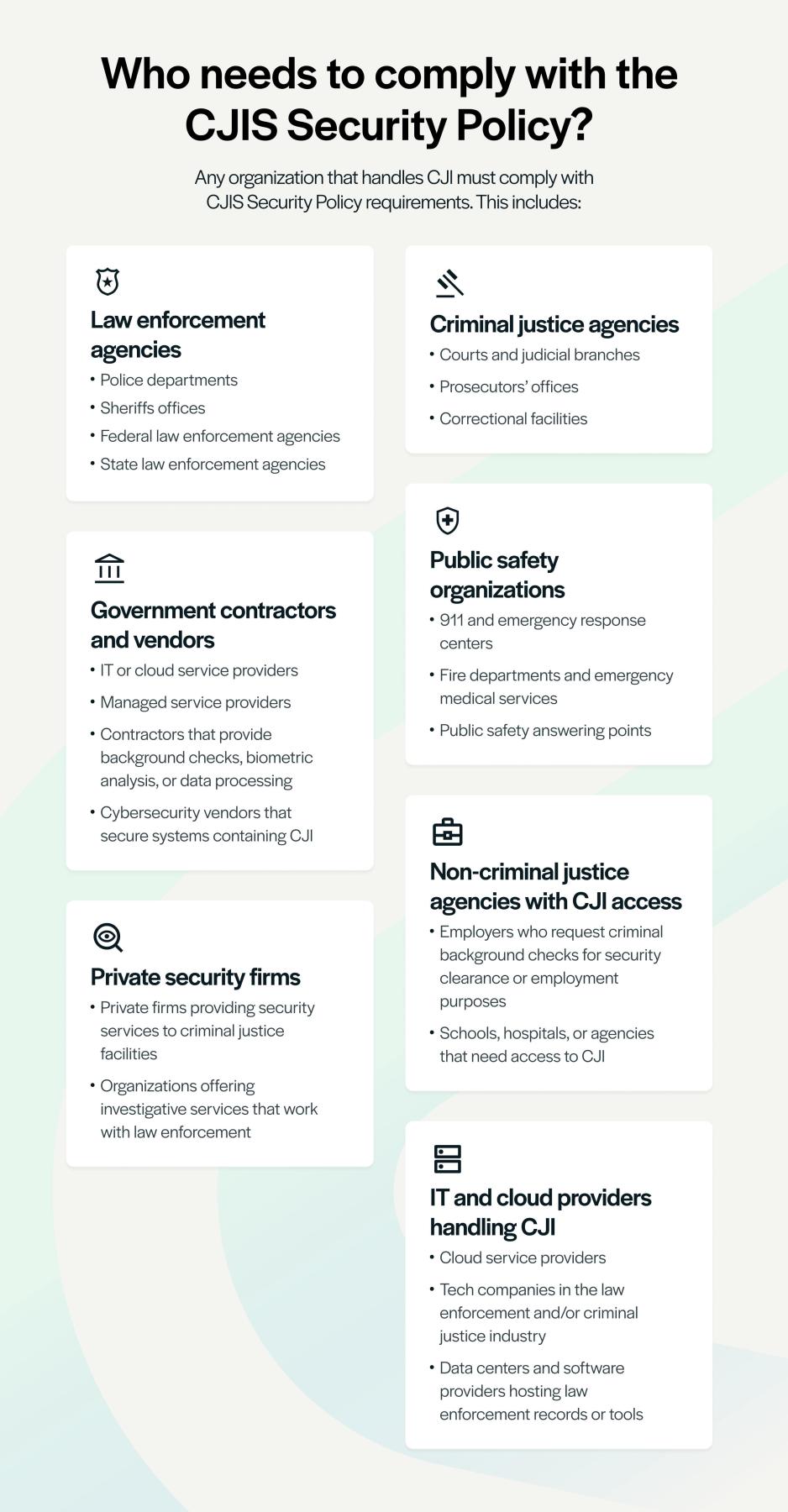
The new requirements include having multi-factor authentication, encryption of data,and supply chain risk management, and audits and logs. This is required not just of police departments but other entities that might have access to police department systems including non-criminal justice agencies, government contractors, and IT service providers.
“Every entity that has the ability to touch police department data – whether that be your Internet provider who has created a cloud-based environment or a third-party IT company or vendor – are now mandated to also comply with these regulations,” Shelton said. “All of those entities now have to have background checks, get their fingerprints done, and take the CJIS test to make sure they understand the rules. They need proper credentials in place. A lot of mom-and-pop shops or your best friend down the road who does your IT does not have the credentialling for this. You have to make sure whoever is protecting your data is keeping up-to-date and meeting these requirements.”
Additionally, Walton said departments are required to have elements of physical security in place such as security cameras monitoring server room, locks or keycard access to rooms containing sensitive data, and the ability to keep records of who accessed what information when.
Officers and vendors are required to do cybersecurity training that meets CJIS standards as well as ensure police computers and laptops meet compliance. Even the emails used by the department must use specific technology on U.S.-based servers. Policies also need to be in place if there ever is a security breach.
